Serie
From Setup to Success: Navigating External Collaboration in Microsoft 365 Like a Pro
1: Best Practices für das Management von B2B Guest Accounts in Microsoft 365 (Du liest diesen Artikel)
Das Management von B2B Guest Accounts in Microsoft 365 ist entscheidend, um Sicherheit und Compliance zu gewährleisten und gleichzeitig eine effiziente Zusammenarbeit zu ermöglichen. Durch die Implementierung von Best Practices stellst du sicher, dass Guest Accounts effektiv und sicher genutzt werden. Im Folgenden findest du zentrale Empfehlungen, inklusive der Gründe, warum sie so wichtig sind.
Guest Accounts mit Conditional Access Policies und Multi-Factor Authentication (MFA) absichern
Conditional Access Policies sind essenziell, um B2B Guest Accounts abzusichern. Indem definiert wird, unter welchen Bedingungen Guest Accounts auf Ressourcen zugreifen dürfen, lässt sich das Risiko unbefugter Zugriffe erheblich reduzieren. Faktoren wie Benutzerstandort, Gerätekonformität oder Risikostufen ermöglichen einen differenzierten Sicherheitsansatz. So wird sichergestellt, dass der Zugriff nur unter sicheren Bedingungen gewährt wird. Diese Granularität ist in einer zunehmend dynamischen und vielfältigen digitalen Umgebung unverzichtbar.
Die Durchsetzung von Multi-Factor Authentication (MFA) für Guest Accounts wird dringend empfohlen. MFA erhöht die Sicherheit, indem mehrere Verifizierungsfaktoren erforderlich sind, bevor auf sensible Informationen zugegriffen werden kann. Dadurch wird das Risiko von Credential Theft deutlich reduziert, da Angreifer mehrere Authentifizierungsfaktoren kompromittieren müssten, um Zugriff zu erhalten.
Multi-Factor Authentication (MFA) für Guest Accounts konfigurieren:
- Öffne das Microsoft Entra Admin Center.
- Navigiere zu Protection und wähle Conditional Access.
- Klicke auf Create policy, um eine neue Conditional-Access-Policy zu erstellen.
- Vergib einen aussagekräftigen Namen für die Policy.
- Unter Assignments:
- Wähle Users and groups > Guest or external users > B2B collaboration guest users.
- Wähle unter Cloud apps die Option All cloud apps als Zielressource.
- Unter Access controls:
- Wähle unter Grant die Option Require multi-factor authentication.
- Setze die Policy zunächst auf Report-only, um die Auswirkungen zu überwachen.
- Nach erfolgreicher Validierung stelle die Policy auf On, um MFA für Guest Accounts aktiv zu erzwingen.
Nicht eingelöste B2B-Einladungen überwachen und verwalten
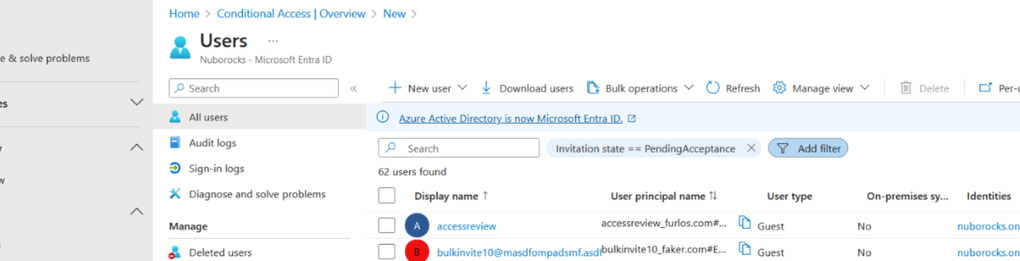
Die Überwachung nicht eingelöster B2B-Einladungen ist entscheidend, um eine sichere und strukturierte digitale Umgebung innerhalb der Organisation aufrechtzuerhalten. Ein nicht eingelöstes B2B-Konto entsteht, wenn eine Einladung an einen externen Benutzer versendet wurde, dieser sie jedoch nicht angenommen oder aktiviert hat. Bleiben solche Einladungen unbeachtet, können Sicherheitsrisiken entstehen – insbesondere dann, wenn potenziell unautorisierter Zugriff auf organisatorische Ressourcen möglich wird.
Eine regelmässige Überprüfung des Status dieser Einladungen hilft dabei, inaktive Einträge frühzeitig zu erkennen. Anschliessend kann mit den Empfängern, die ihre Einladung noch nicht eingelöst haben, Kontakt aufgenommen werden. Dieser proaktive Ansatz stellt sicher, dass ausschliesslich aktive und eingebundene Benutzer Zugriff auf freigegebene Ressourcen erhalten. Das verbessert sowohl die Sicherheit als auch das Ressourcenmanagement. Reagieren Empfänger nicht innerhalb eines definierten Zeitraums, empfiehlt es sich, diese Einträge zu löschen. Dadurch bleibt das System sauber und sicher, und potenzielle Schwachstellen werden wirksam minimiert.
Durch eine konsequente Überwachung und Verwaltung nicht eingelöster B2B-Einladungen bleibt die Zusammenarbeit effizient, während sensible Informationen zuverlässig vor unbefugtem Zugriff geschützt werden.
Nicht eingelöste Einladungen lassen sich in Entra ID identifizieren, indem die Benutzerkonten überprüft und der Status "Invitation state == !PendingAcceptance" kontrolliert wird.
Terms of Use für Guest Access durchsetzen
Von Guest-Benutzern zu verlangen, dass sie die Datenschutzrichtlinien und Nutzungsbedingungen der Organisation prüfen und akzeptieren, bevor sie Zugriff erhalten, ist essenziell für Compliance und Transparenz. Diese Praxis stellt sicher, dass alle Benutzer die Bedingungen kennen und akzeptieren, unter denen ihnen Zugriff gewährt wird. Dadurch lassen sich rechtliche Risiken und Missverständnisse vermeiden. Eine regelmässige erneute Bestätigung der Richtlinien sorgt zudem für fortlaufende Compliance mit regulatorischen Anforderungen und stellt sicher, dass Benutzer über Änderungen informiert bleiben.
Um Terms of Use zu erstellen, muss das Dokument zunächst in Word oder einem anderen Autorentool erstellt und anschliessend als PDF-Datei gespeichert werden. Diese Datei kann danach in Microsoft Entra ID hochgeladen werden.
Microsoft Entra Terms of Use erstellen:
- Öffne das Microsoft Entra Admin Center.
- Erweitere Protection und wähle Conditional Access.
- Wähle Terms of use.
- Klicke auf New terms.
- Vergib einen Namen.
- Lade unter Terms of use document die zuvor erstellte PDF-Datei hoch.
- Wähle die Sprache für das Dokument aus.
- Definiere einen Display name.
- Setze Require users to expand the terms of use auf On.
- Wähle unter Conditional Access, in der Liste Enforce with Conditional Access policy template, die Option Create conditional access policy later.
- Klicke auf Create.
Nachdem die Terms of Use erstellt wurden, muss im nächsten Schritt eine Conditional Access Policy konfiguriert werden, damit diese den Guest-Benutzern angezeigt werden.
Eine Conditional Access Policy erstellen:
- Öffne im Microsoft Entra Admin Center unter Protection den Bereich Conditional Access.
- Wähle auf der Seite Conditional Access | Overview die Option Create new policy.
- Vergib im Feld Name einen aussagekräftigen Namen.
- Klicke auf Users.
- Wähle Select users and groups und aktiviere das Kontrollkästchen Guest or external users.
- Wähle im Dropdown-Menü B2B collaboration guest users und B2B collaboration member users aus.
- Klicke auf Target resources.
- Wähle im Tab Include die Option Select apps und klicke auf Select.
- Wähle im Auswahlfenster Office 365 aus und bestätige mit Select.
- Klicke auf Grant.
- Wähle im Bereich Grant die zuvor erstellten Terms of use aus und bestätige mit Select.
- Setze unter Enable policy die Option auf On und klicke auf Create.
Ab diesem Zeitpunkt müssen Guest-Benutzer beim ersten Zugriff auf Inhalte, ein Team oder eine Site in der Organisation die Terms of Use akzeptieren.
Sponsoren für Guest Accounts festlegen
Das Zuweisen von Verantwortlichen (Ownern) für Guest Accounts vereinfacht das Management und die Nachvollziehbarkeit. Owner sind für die regelmässige Überprüfung und Validierung von Guest Accounts zuständig und stellen sicher, dass der gewährte Zugriff weiterhin gerechtfertigt und angemessen ist. Diese Praxis trägt zu einer strukturierten und sicheren Umgebung bei, in der jedes Konto aktiv verwaltet und überwacht wird.
Microsoft hat dafür das Konzept des Business Sponsors eingeführt. Damit lässt sich nachvollziehen, wer innerhalb der Organisation für einen bestimmten Guest Account verantwortlich ist. Weitere Informationen dazu findest du hier: Add sponsors to a guest user in the Microsoft Entra admin center - External ID - Microsoft Entra External ID | Microsoft Learn.
Regelmässige Access Reviews durchführen
Regelmässige Access Reviews sind entscheidend, um sicherzustellen, dass die Berechtigungen von Guest Accounts weiterhin den aktuellen Anforderungen der Zusammenarbeit entsprechen. Durch eine kontinuierliche Überprüfung der Zugriffsrechte lassen sich Abweichungen schnell erkennen und korrigieren. So wird gewährleistet, dass ausschliesslich Personen Zugriff haben, die diesen tatsächlich benötigen. Automatisierte Benachrichtigungen an Administratoren zur regelmässigen Überprüfung der Zugriffsberechtigungen sorgen für einen konsistenten und zuverlässigen Prozess.
Für die Governance von Guest Accounts können Microsoft Entra Access Review Packages eingesetzt werden. Beachte dabei, dass unter Umständen Microsoft Entra ID P2- oder Microsoft Entra ID Governance-Lizenzen erforderlich sind.
Expiration Policies für inaktive Guest Accounts implementieren
Durch die Implementierung von Expiration Policies wird sichergestellt, dass Zugriffsrechte nicht unbegrenzt bestehen bleiben. Werden Richtlinien definiert, die den Zugriff nach einem bestimmten Zeitraum automatisch auslaufen lassen, lässt sich das Risiko veralteter oder unnötiger Berechtigungen deutlich reduzieren. Das automatische Deaktivieren von Accounts, die sich innerhalb eines festgelegten Zeitraums nicht angemeldet haben, erhöht die Sicherheit zusätzlich, da die Anzahl ungenutzter, aber aktiver Konten minimiert wird. Accounts, die seit mehr als drei Monaten deaktiviert sind, sollten gelöscht werden, um eine saubere und sichere Umgebung ohne verwaiste Konten zu gewährleisten.
Inaktive Guest Accounts lassen sich mit folgendem PowerShell-Skript identifizieren:
# Install the Microsoft Graph modules
Install-Module -Name Microsoft.Graph.Identity.SignIns -Force
Install-Module -Name Microsoft.Graph.Users -Force
Connect-MgGraph -Scopes 'User.Read.All'# Get guest users who haven't signed in for more than 180 days
$DateCutoff = (Get-Date).AddDays(-180)
$InactiveGuests = Get-MgUser -Filter "userType eq 'Guest'" | Where-Object { $_.LastSignInDateTime -lt $DateCutoff }
$InactiveGuests | Select-Object DisplayName, UserPrincipalName, LastSignInDateTime
$InactiveGuestsEinen effizienten Guest-Offboarding-Prozess implementieren
Deaktiviere oder lösche B2B Accounts, die nicht mehr mit deiner Organisation zusammenarbeiten. Business Sponsoren die Möglichkeit zu geben, Guest Accounts zu deaktivieren oder zu löschen, ist ein wichtiger Bestandteil einer sicheren und compliance-konformen Umgebung. So wird sichergestellt, dass der Zugriff eines Guests unmittelbar entzogen werden kann, sobald die Zusammenarbeit endet. Dadurch wird das Risiko unbefugter Zugriffe deutlich reduziert. Automatisierte Prozesse zur Deaktivierung oder Löschung inaktiver Accounts unterstützen diesen Ansatz zusätzlich. Sie sorgen dafür, dass verwaiste oder ungenutzte Konten kein dauerhaftes Sicherheitsrisiko darstellen.
Benutzer zu Security Best Practices schulen
Regelmässige Security-Awareness-Schulungen für interne und externe Benutzer sind essenziell für eine starke Sicherheitsstrategie. Diese Trainings stellen sicher, dass alle Benutzer – einschliesslich Guest Accounts – über aktuelle Bedrohungen und Best Practices informiert sind. Wird Security-Training als verpflichtender Bestandteil des Onboardings für Guest-Benutzer integriert, verfügen alle Beteiligten über das notwendige Wissen, um sensible Informationen zu schützen. Kontinuierliche und regelmässige Schulungen halten Benutzer über neue Bedrohungen und Sicherheitsmassnahmen auf dem Laufenden und fördern eine nachhaltige Sicherheitskultur.
Wie lassen sich B2B-Governance-Best-Practices in der Praxis umsetzen?
Zusammenfassend ist die Implementierung von Best Practices für das Management von B2B Guest Accounts in Microsoft 365 entscheidend für Sicherheit, Compliance und eine effiziente Zusammenarbeit innerhalb der Organisation. Von der Durchsetzung von Multi-Factor Authentication (MFA) über die Überwachung von Guest-Einladungen bis hin zur Zuweisung von Ownern und regelmässigen Access Reviews – all diese Massnahmen tragen zu einer strukturierten und sicheren Umgebung bei.
Für eine erweiterte Governance und eine vereinfachte Verwaltung bietet sich die Nutzung der EasyLife 365 Collaboration Guest Management Feature an. Diese Integration ermöglicht einen strukturierten und effizienten Umgang mit Guest Accounts und stellt leistungsstarke Werkzeuge zur Verfügung, um Zugriffe sicher zu verwalten und zu überwachen.
Noch unsicher wo du starten sollst? Wirf einen Blick in unsere Schritt-für-Schritt-Anleitungen.