Series
Proven Practices for Managing App Registrations in Entra ID
1: What Are App Registrations in Microsoft Entra ID?
2: Assigning App Ownership and Avoiding Shared Registrations in Microsoft Entra ID (you are reading this article)
3: Credential and Permission Management for App Registrations in Entra ID
4: Controlling App Registration Growth in Microsoft Entra ID
Once you understand what app registrations are and why they matter (see Part 1 of this series), the next step is tightening your governance around them. The technical setup is only part of the story. Without clear ownership and the right structure, things can spiral quickly. d In this post, we’ll walk through three essential best practices that lay the groundwork for scalable identity governance in Microsoft Entra ID:
- Assigning technical ownership
- Defining business accountability through sponsors
- Avoiding sharing one app registration across environments
These practices help you reduce risk, improve clarity, and lay the groundwork for scalable identity governance.
Best Practice 1: Assign Technical Ownership in Entra ID
One of the most important aspects of managing app registrations in Microsoft Entra ID is ensuring that each application has clearly defined ownership. This means assigning responsibility for the app to a specific person or team within your organization.
Without a clear owner, it becomes difficult to manage the app’s configuration, review its permissions, rotate credentials, or make informed decisions about its continued use. Over time, this can lead to unmanaged or forgotten apps with excessive access, posing a real security and compliance risk.
In Microsoft Entra ID, you can formally assign owners using the Owners setting in the app registration. This is managed through the Owners blade in the Entra admin center. Owners have full administrative control over the application registration. They can:
- Modify configuration settings
- Update or replace client secrets and certificates
- Change API permissions
- Adjust redirect URLs and branding
Essentially, they act as delegated administrators for that specific app. However, it is important to note that Entra ID does not automatically send notifications to these owners about expiring secrets or other events. They must proactively monitor the app or rely on external tooling to stay informed.
In practice, assigning technical owners ensures that someone is accountable for the technical integrity and maintenance of the app. But technical ownership is often only part of the picture. Most applications also need business ownership, meaning someone who understands why the app exists, who uses it, what data it processes, and whether it still provides business value. Tracking both technical and business responsibility is essential for strong identity governance.
Best Practice 2: Track Business Accountability with Sponsors
This gap became clear early in the development of EasyLife 365 Identity. While technical ownership was often inconsistent, business ownership was rarely captured at all. Applications would remain in tenants without anyone clearly accountable for them, making it hard to manage credentials, permissions, or even decide whether the app was still necessary.
To address this, we introduced the concept of sponsors from the very beginning. We wanted a way to track non-technical accountability. Those people who understand the business case behind the app, who uses it, and what value it delivers. Whether it’s a department lead, a process owner, or another stakeholder in the business, these sponsors provide critical visibility into why the app exists and how it supports daily work.
EasyLife 365 Identity allows you to assign these roles clearly and track who holds business accountability. It helps you connect each application to the people who rely on it, making responsibility visible across the organization.
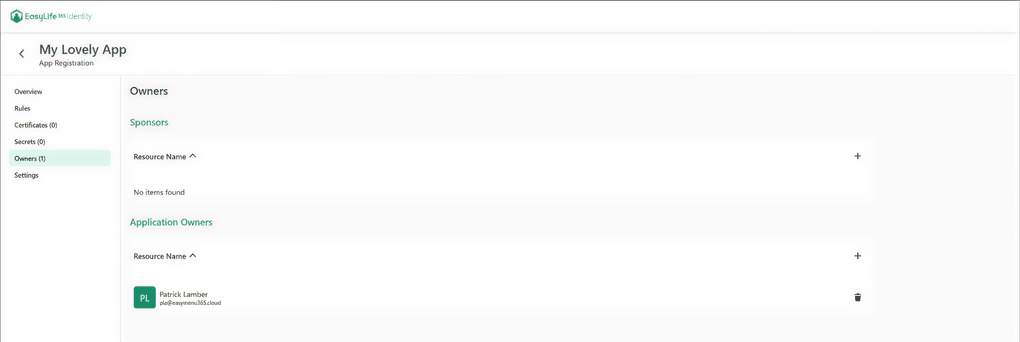
|
|---|
| Assigning business sponsors in EasyLife 365 Identity. |
Beyond simply assigning roles, EasyLife 365 Identity also allows you to delegate permissions to sponsors or other users in a granular way. This means you can grant specific people the ability to manage an app or perform defined actions, without giving them full access to the broader Entra ID environment.
This kind of delegated control is especially useful in larger organizations, where central IT teams need to maintain oversight while enabling local teams to manage their own applications securely and efficiently.
Because in the end, ownership is not just a checkbox. It is a critical control that ensures every application in your identity environment has clear accountability, both technical and business. Whether managed directly in Entra ID or enhanced through EasyLife 365 Identity, strong ownership practices help prevent configuration drift, reduce the risk of privilege misuse, and support better decision-making throughout the application lifecycle.
Best Practice 3: Don’t Share One App Registration Across Environments
In a typical application development process, different environments are used to support the lifecycle of the application. These usually include development, testing, and production.
Each environment serves a specific purpose:
- Development is where you build and experiment
- Testing is used for quality assurance, integration, and validation
- Production is the live system used by end users
While these environments may run similar versions of an application, they often require different access controls, monitoring configurations, and security boundaries.
A common mistake, especially in smaller teams or early-stage projects, is to use a single app registration in Microsoft Entra ID across all these environments. At first, this might seem more convenient, because it reduces the number of registrations to manage. However, this practice creates several significant risks.
Using one app registration across multiple environments introduces several serious risks:
- Shared credentials: Secrets or certificates used in development are also valid in production. If a dev environment is compromised, attackers could gain access to production systems.
- No separation of permissions: API permissions aren’t scoped by environment. It’s hard to enforce least privilege or to track which environment is accessing what.
- Loss of visibility: All sign-ins, token requests, and permission grants are logged under the same application ID. You can’t easily tell which environment is doing what, making it harder to audit, monitor, or troubleshoot.
Using a single app registration across environments undermines both security and operational clarity. Without clear separation, it becomes significantly harder to monitor application behavior or audit access patterns effectively. Small issues in development can ripple into production without leaving an obvious trail.
Conclusion: Strong Foundations for Scalable App Governance in Microsoft Entra ID
Governance starts with structure. Assigning the right people to each application and avoiding shared registrations gives you the visibility and control needed to manage app identities with confidence.
EasyLife 365 Identity helps you put these foundations in place by:
- Assigning and tracking business sponsors
- Assigning and tracking owners
- Grouping related app registrations
In Part 3, we will focus on credentials and permissions. You will learn how to avoid over-permissioned apps, rotate secrets safely, and take back control over who can register applications in your tenant. Stay tuned. It’s a practical next step toward stronger control over app access and configuration.