Series
From Setup to Success: Navigating External Collaboration in Microsoft 365 Like a Pro
1: Introducing External Collaboration in Microsoft 365
2: Configuring External Collaboration in Microsoft 365: Settings, Security & Guest Access
3: Best Practices for Managing B2B Guest Accounts in Microsoft 365 (you are reading this article)
Managing B2B guest accounts in Microsoft 365 is crucial for maintaining security and compliance while enabling efficient collaboration. Implementing best practices ensures that guest accounts are used effectively and safely. Here are some essential practices to consider, along with explanations of why they are important.
Secure Guest Accounts with Conditional Access Policies and Multi-Factor Authentication (MFA)
Conditional access policies are crucial for securing B2B guest accounts. By specifying conditions under which these accounts can access resources, organizations can significantly reduce the risk of unauthorized access. Leveraging factors such as user location, device compliance, and risk levels allows for a nuanced security approach, ensuring access is granted only under secure conditions. This granularity is essential in today’s diverse and dynamic digital environment.
Enforcing multi-factor authentication (MFA) for guest accounts is highly recommended. MFA enhances security by requiring guests to provide multiple forms of verification before accessing sensitive information. This strategy mitigates the risk of credential theft, as an attacker would need to compromise multiple factors to gain access.
To enforce Multi-Factor Authentication (MFA) for guest accounts, follow these refined steps:
- Go to Microsoft Entra admin center to access the Microsoft Entra admin center.
- Navigate to Protection and select Conditional Access.
- Click on Create policy to initiate a new Conditional Access policy.
- Provide a descriptive Name for the policy.
- Under Assignments:
- Select Users and groups > Guest or external users > B2B collaboration guest users.
- Choose All cloud apps as the target resource under Cloud apps.
- In Access controls, configure:
- Select Require multi-factor authentication under Grant.
- Initially, set the policy to Report-only to monitor its impact.
- Once validated, switch the policy to On to enforce MFA for guest accounts.Guest Onboarding
Monitor and Manage Non-Redeemed B2B Invitations
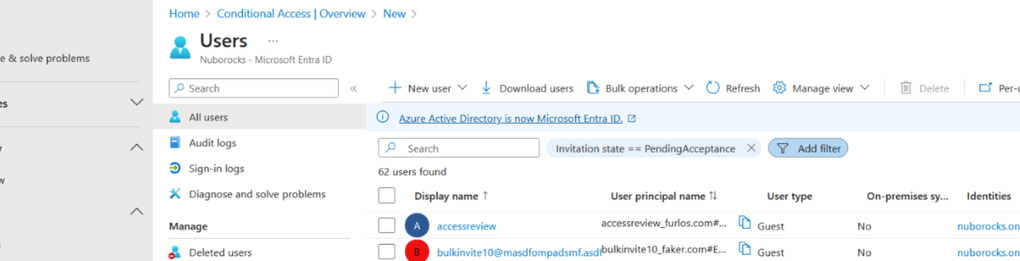
Monitoring non-redeemed B2B invitations is crucial for maintaining a secure and organized digital environment within organizations. A non-redeemed B2B account refers to an invitation extended to an external user that has not been accepted or activated. These invitations, if left unattended, can pose security risks by potentially allowing unauthorized access to organizational resources.
Regularly checking the status of these invitations helps identify inactive entries. Organizations can then follow up with the recipients who have not yet redeemed their invitations. This proactive approach ensures that only active and engaged users have access to shared resources, enhancing security and resource management. If recipients do not respond within a reasonable timeframe, deleting these entries is recommended to keep the system clean and secure, minimizing potential vulnerabilities. By monitoring and managing non-redeemed B2B invitations effectively, organizations can maintain efficiency in collaboration while safeguarding sensitive information from unauthorized access.
You can identify in Entra ID guest accounts that haven’t redeemed their invitation by checking your user accounts and verifying the “Invitation state == !PendingAcceptance”.
Enforce Terms of Use for Guest Access
Requiring guest users to review and accept the organization’s privacy policies and terms of use before gaining access is essential for compliance and transparency. This practice ensures that all users are aware of and agree to the terms under which they are granted access, which can help prevent legal issues and misunderstandings. Incorporating periodic re-acceptance of these policies ensures ongoing compliance with regulatory requirements and keeps users informed of any changes.
To create a term of use, you first need to create the document in Word or another authoring program, and then save it as a .pdf file. This file can then be uploaded to Microsoft Entra ID.
To create a Microsoft Entra term of use:
- Open the Microsoft Entra admin center.
- Expand Protection, and then select Conditional Access.
- Select Terms of use.
- Select New terms.
- Type a Name.
- For Terms of use document, browse to the pdf file that you created and select it.
- Select the language for your terms of use document.
- Type a display name.
- Set Require users to expand the terms of use to On.
- Under Conditional Access, in the Enforce with Conditional Access policy template list choose Create conditional access policy later.
- Select Create.
Once you've created the terms of use, the next step is to create a conditional access policy that displays the terms of use to guests.
To create a conditional access policy:
- In the Microsoft Entra admin center, under Protection, select Conditional access.
- On the Conditional Access | Overview page, select Create new policy.
- In the Name box, type a name.
- Select the Users link.
- Choose Select users and groups, and then select the Guest or external users check box.
- In the dropdown, select B2B collaboration guest users and B2B collaboration member users.
- Select the Target resources link.
- On the Include tab, choose Select apps, and then click the Select link.
- On the Select blade, select Office 365, then click Select.
- Select the Grant link.
- On the Grant blade, select the check box for the terms of use that you created, and then click Select.
- Under Enable policy, select On, and then select Create.
Now, the first time a guest attempts to access content or a team or site in your organization, they'll be required to accept the terms of use.
Assign Sponsors to Guest Accounts
Assigning owners to guest accounts streamlines management and accountability. Owners are responsible for the periodic review and validation of guest accounts, ensuring that access is justified and appropriate. This practice helps maintain a structured and secure system, where each account is actively managed and monitored.
Microsoft introduced the concept of business sponsor that allows you to track who is responsible for that guest account. You can learn more about this here. Add sponsors to a guest user in the Microsoft Entra admin center - External ID - Microsoft Entra External ID | Microsoft Learn.
Conduct Regular Access Reviews
Regular access reviews are crucial for ensuring that guest account permissions align with current collaboration needs. By auditing access regularly, organizations can identify and address any discrepancies, ensuring that only those who need access have it. Automatic notifications to administrators for regular review of access permissions keep the process consistent and reliable.
You could consider using Microsoft Entra access review packages to govern the access review of guest accounts. Please note that you might require Microsoft Entra ID P2 or Microsoft Entra ID Governance licenses to accomplish this goal.
Implement Expiration Policies for Inactive Guest Accounts
Implementing expiration policies for guest accounts ensures that access is not granted indefinitely. By setting policies that automatically expire access after a specified period, organizations can minimize the risk of outdated and unnecessary access. Automatically disabling accounts that haven’t signed in within a set timeframe further enhances security by reducing the number of active accounts that are not being used. Deleting accounts that have been disabled for three months helps maintain a clean and secure environment, free of dormant accounts.
You can identify inactive guest accounts with this PowerShell script:
# Install the Microsoft Graph modules
Install-Module -Name Microsoft.Graph.Identity.SignIns -Force
Install-Module -Name Microsoft.Graph.Users -Force
Connect-MgGraph -Scopes 'User.Read.All'# Get guest users who haven't signed in for more than 180 days
$DateCutoff = (Get-Date).AddDays(-180)
$InactiveGuests = Get-MgUser -Filter "userType eq 'Guest'" | Where-Object { $_.LastSignInDateTime -lt $DateCutoff }
$InactiveGuests | Select-Object DisplayName, UserPrincipalName, LastSignInDateTime
$InactiveGuestsEfficient Guest Offboarding Processes
Disable/Delete the B2B accounts that are not collaborating with you anymore. Allowing business sponsors to disable or delete guest accounts is an important aspect of maintaining security and compliance. This capability ensures that when a guest’s collaboration period ends, their access can be promptly revoked, minimizing the risk of unauthorized access. Automated processes for disabling and deleting inactive accounts further enhance this practice, ensuring that dormant accounts do not pose a security risk.
Educate Users on Security Best Practices
Conducting regular security awareness sessions for both internal and external users is vital for maintaining a robust security posture. These sessions ensure that all users, including guests, are aware of the latest security threats and best practices. Making security training a mandatory part of onboarding for all guest users ensures that everyone is equipped with the knowledge needed to protect sensitive information. Ongoing education keeps users informed about new threats and security measures, fostering a culture of security awareness.
Wrapping it up
In conclusion, implementing best practices for managing B2B guest accounts in Microsoft 365 is crucial for maintaining security, compliance, and efficient collaboration within organizations. From enforcing multi-factor authentication and monitoring guest invitations to assigning owners and conducting regular access reviews, these practices ensure a structured and secure environment. For enhanced governance and ease of management, consider leveraging the EasyLife 365 Collaboration Guest Management Feature. This integration provides a streamlined approach to handling guest accounts, empowering organizations and users alike with effective tools to manage and monitor access securely.